Effective way to test Azure cloud services during microservices development from localhost in JAVA Quarkus framework
10. 5. 2024

Modern cloud development consist of ecosystem of cooperating and interacting microservices which are typically deployed in the cloud Kubernetes cluster. They need to interoperate with each other as well as with native cloud services such as Keys and password stores, databases, AI services, blob storage, streaming services etc. The essential part of the security is to store all secrets, password and keys in the dedicated storage of the cloud. They have the strongest state of the art industry protection and offer best practices as password rotation, encryption, expiration.
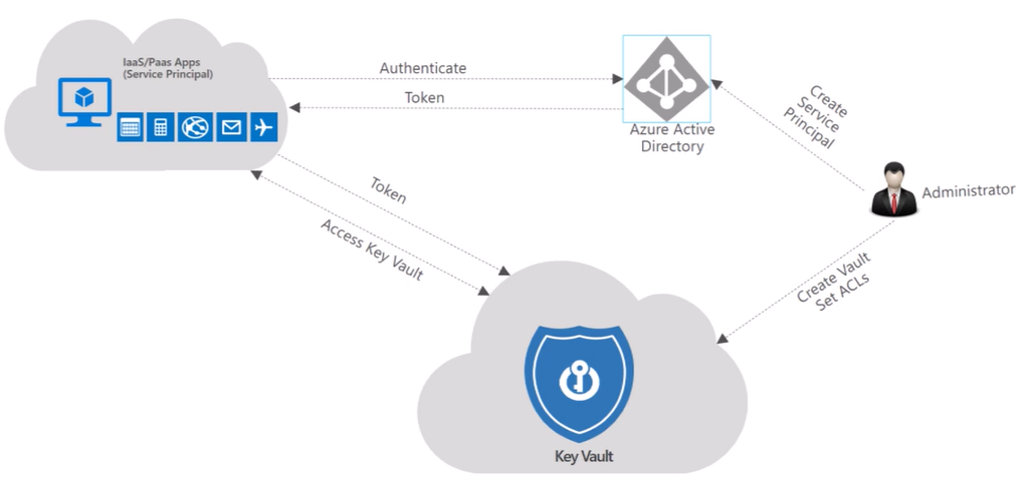
In this blog we are sharing how to use Azure cloud KeyVault service during development of the microservice component. The must best practice during development in the Azure cloud to store and read bearer tokens, secrets, password and private and public keys to use KeyVault service . The service can generate private/public keys, the keys can be imported, secrets have expiration date. When microservice is communicating with services and other components, best practice is to use public key to encrypt the payload and private key to decrypt. These keys can only be stored in KeyVault in Azure cloud ecosystem.
During development there is a need to test the functionality from localhost to Azure cloud services. In the localhost mode there is a need to read secrets and keys to decrypt/encrypt payloads and contact other APIs. Comfortable approach is to put the tokens or keys in the config file or code. The code is then commited to gitlab where it is readable. So this should be done only with exception and before commiting the code to gitlab should all secrets be erased.
Recommended approach is to configure localhost enviroment to access Azure cloud services. We will demonstrate it in the JAVA Quarkus framework. Teh approach is to user Service Principal which is allowed to access Key Vault Azure service
The steps are :
- Register the App in the Azure Entra ID service
- Generate client secret for the app
- Get the tennant id, client id, client secret and service url to configure Service Principal in the local development
- Add the app to the key vault reader role in the Access control /IAM/ for role based approach in the Azure or add Access policy to be able to read the keys for the app client id.
- Edit the application properties file or use the attributes to create ClientCredentialBuilder class to access the key vault.
- Use the Azure cloud service and test it in the localhost enviroment
Register the App in the Azure Entra ID :
Click new App registration :
Mark the the tenant id, client id and generate client secret. The add the app client id to the key vault reader role or allow it in the access policies to read the key vault.
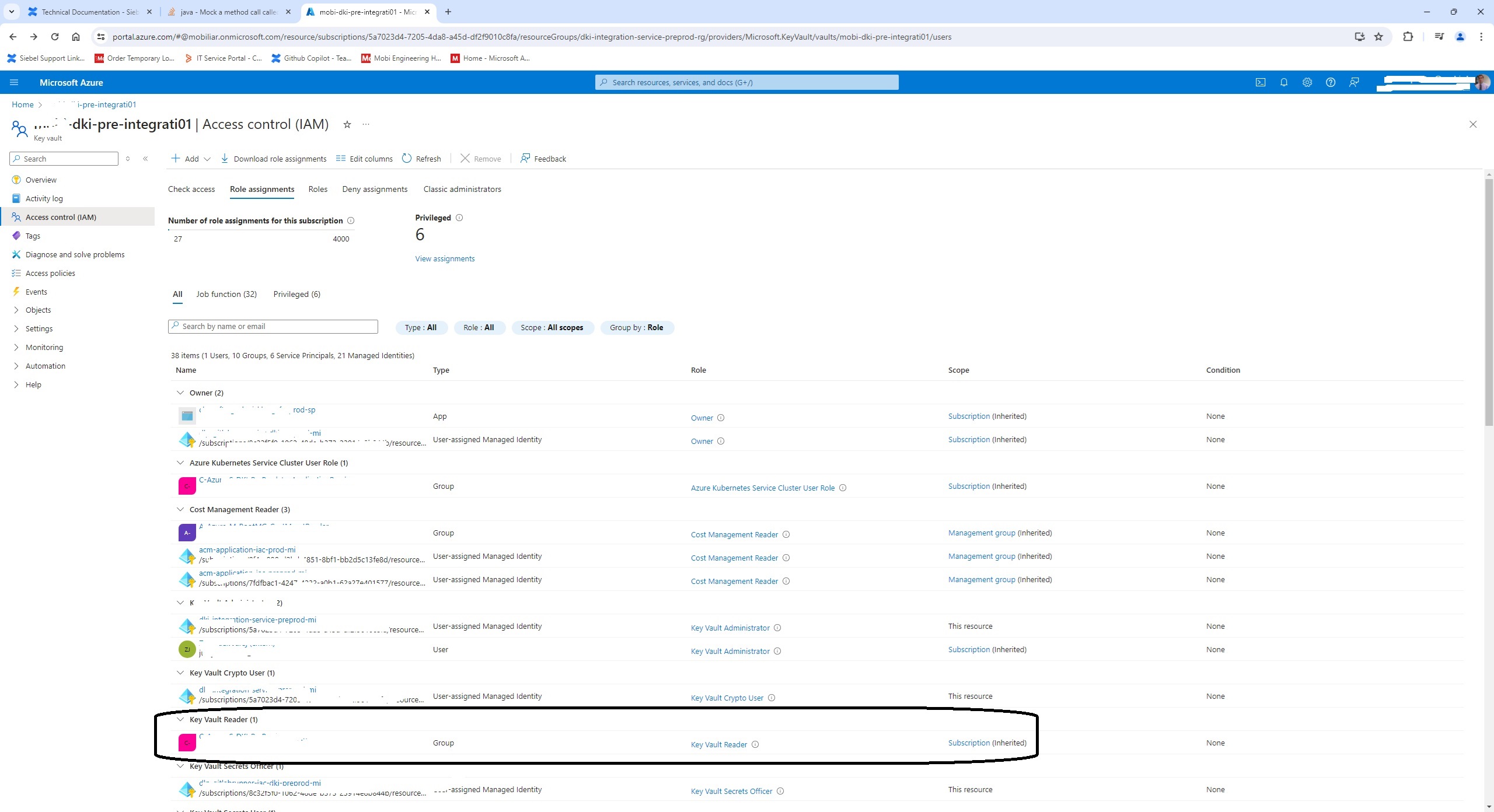
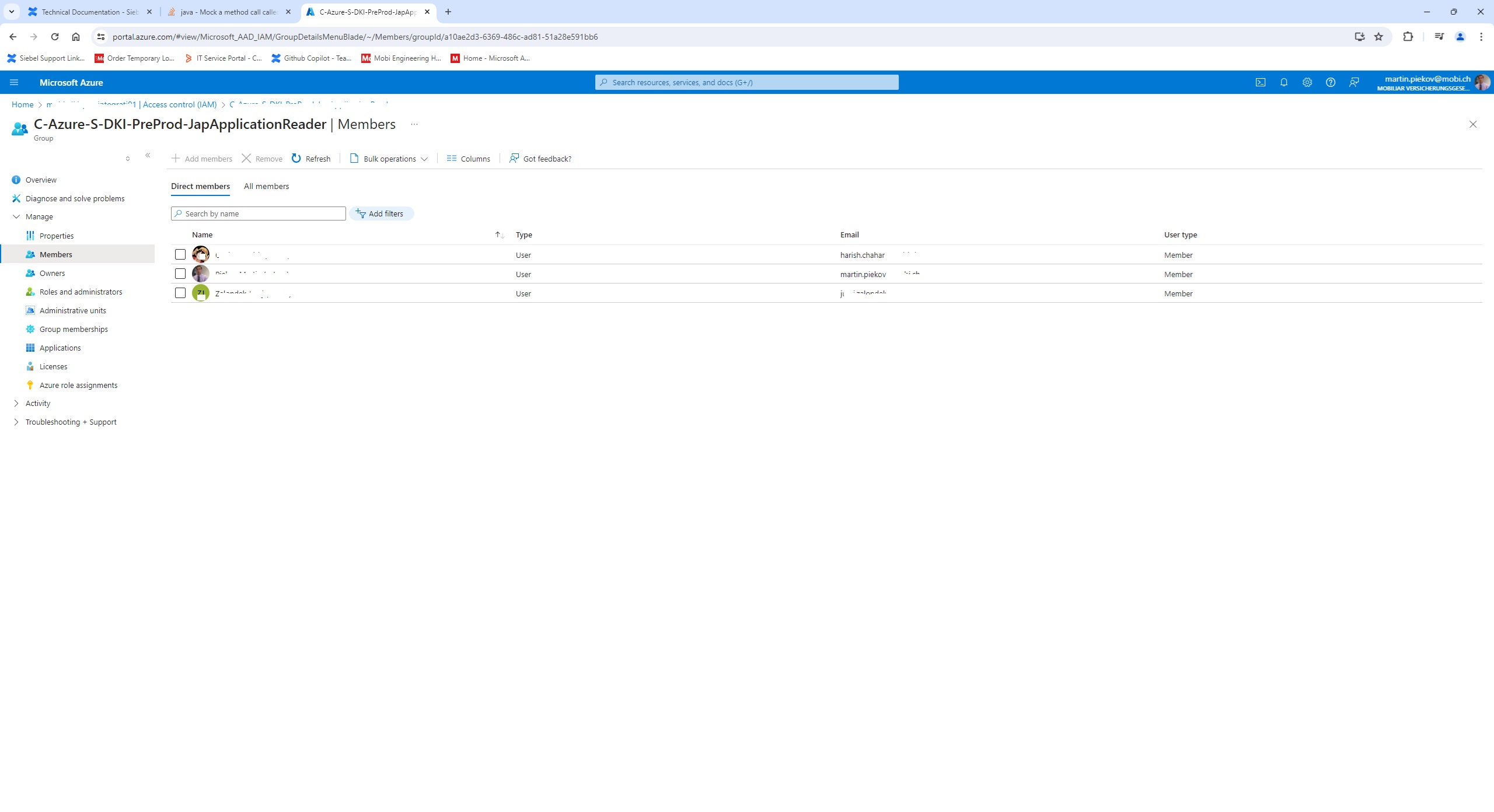
Now example how to access Azure Key Vault :
public AzureKeyVaultService() {
ClientSecretCredential clientSecretCredential = new ClientSecretCredentialBuilder()
.clientId("dccxxxxb5d")
.clientSecret("dffdfd8Qxxx-adI")
.tenantId("dddd1-dd3a-dd7-9e9f-dddddd4")
.build();
keyClient = new KeyClientBuilder()
.vaultUrl(https://yourkeyvaulturl) // replace with your vault URL
.credential(clientSecretCredential)
.buildClient();
}
public String getKey(String keyName) {
KeyVaultKey key = keyClient.getKey(keyName);
return key.getKey().toString();
}
In your code you can obtain the private key by
dddPrivateKey = azureKeyVaultService.getKey("dddd-private-key");
Contact us for more support of cloud native development either in Azure, AWS or OCI clouds.
Späť na Blog