Debugging outbound http comunication in Siebel IP17+.
6. 6. 2024

Previously we have already written about how to configure logging for tomcats in the siebel enviroment
During implementation of the outbound webservices or rest services it is often needed to debug the http communication between siebel enviroment and endpoint of the producer.
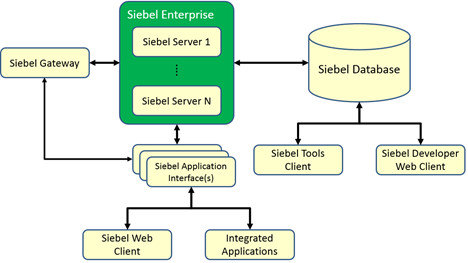
The architecture and topology of the siebel crm for the outnbound call is starting in application object manager /AOM/ and goes with http localhost. Prior the version Siebel IP16 it was all tracable in AOM log by setting the correct parameters for webservice logging .To trace all the communication between sienel crm enviroment and outbound webservice endpoint following needs to be done :
In the catalina.out are after setting
-Djavax.net.debug=all -Dssl.debug=true -Djava.security.debug=certpath
in setenv.sh which is in
..siebeldir/applicationcontainer_internal/bin
extend the CATALINA_OPTS variable with
-Djavax.net.debug=all -Dssl.debug=true -Djava.security.debug=certpath.
During the analysis of the catalina.out log you may find following error :
[SIEBEL ERROR] Thread[http-nio-9012-exec-3,5,main] [2024-04-29 14:53:32.144] [EAI_HTTP_OUTBOUND] Error while writing request body to Outbound URL:
java.net.SocketException: Connection reset
Also described in the
Outbound Web Service Error on OCI: [EAI_HTTP_OUTBOUND] Error while writing request body to Outbound URL: java.net.SocketException: Connection reset (Doc ID 2866927.1)
One of the solution is to set the proxy in the tomcat for the outnound http communication outside org subnet.
How To Add Proxy Server Settings To EAI HTTP Transport, Javacontainer And Application Container (Doc ID 1383419.1)
-Dhttps.proxyHost=dirproxy.mobi.ch -Dhttps.proxyPort=8080 -Dhttp.proxyHost=dirproxy.mobi.ch -Dhttp.proxyPort=8080
One of the error reasons can be missing certificate in the keystore
Siebel Outbound Web Service Fails With sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target (Doc ID 2657414.1)
Here is the complete configuration in the setenv.sh
#!/bin/sh
#
# ENVARS for Tomcat and TDS environment
#
echo "Inside setenv.sh"
PRGDIR=`dirname "$0"`
JRE_HOME="$PRGDIR/./../../jre"
echo "Using JRE_HOME as $JRE_HOME"
CLASSPATH="$CATALINA_HOME/webapps"
export UMASK="0022"
. "/data/siebel/sieb_cfg/env_vars.sh"
. "$RELEASE_HOME/maintenance/sieblsys/bin/sieblsys.sh"
JAVA_OPTS="-verbosegc -XX:+PrintGCDateStamps -XX:+PrintTenuringDistribution -Xms12g -Xmx12g"
JAVA_OPTS=" -XX:+PrintGCDetails -XX:+PrintGCTimeStamps -XX:+PrintHeapAtGC -Xloggc:/app/siebel/sieb/applicationcontainer_internal/logs/gc.log -Dlog4j2.formatMsgNoLookups=true"
JAVA_OPTS=" -XX:+HeapDumpOnOutOfMemoryError -XX:HeapDumpPath=/app/siebel/sieb/applicationcontainer_internal/logs/"
CATALINA_OPTS="-Dhttps.proxyHost=xxxx -Dhttps.proxyPort=1111 -Dhttp.proxyHost=xxxx -Dhttp.proxyPort=1111 -Djavax.net.debug=all -Dssl.debug=true -Djava.security.debug=certpath -Dcatalina.home=/app/siebel/sieb/applicationcontainer_internal -Djavax.net.ssl.trustStore=/app/siebel/sieb/applicationcontainer_internal/siebelcerts/umobi_truststore.jks -Djavax.net.ssl.trustStorePassword=$TRUSTSTORE_PW -Djavax.net.ssl.keyStore=/app/siebel/sieb/applicationcontainer_internal/siebelcerts/Z100067_umobi.jks -Djavax.net.ssl.keyStorePassword=$JMSUSER_PW -agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=8000 -Dfile.encoding=UTF-8 -Dkafka.keyStore=/app/siebel/sieb/applicationcontainer_internal/siebelcerts/Z101152_umobi.jks -Dkafka.keyStorePassword=$KAFKAUSER_PW -Dkafka.trustStore=/app/siebel/sieb/applicationcontainer_internal/siebelcerts/kafkaDevTruststore.jks -Dkafka.trustStorePassword=$KAFKATRUSTSTORE_PW -Dlog4j2.formatMsgNoLookups=true"
CATALINA_OPTS="-Djavax.net.ssl.keyStoreAlias=ld1t026c $CATALINA_OPTS"
Späť na Blog