Setup, test and validate OAuth2 authentication access of Azure Cloud Exchange POP3 accounts
22. 11. 2022

Microsoft has announced, Deprecation of Basic authentication in Exchange Online. It means that Basic Authentication in Exchange Online for POP, IMAP, Remote PowerShell, Exchange Web Services, Outlook for Windows, Mac will be finally disabled after December 31, 2022. After this time, OAuth2 authentication will be for above mentioned protocol and services enabled only.
SMTP Auth as mentioned in Basic Authentication and Exchange Online – July Update - Microsoft Tech Community will not be completely disabling for those customers who still wants to use it.
Many customers who use Azure (Online) Exchange will face the problem to implement OAuth2 authentication for downloading emails. For Oracle Siebel CRM customers, who use inbound emails we have provided the blog: “Cloud Azure integration for Emails with Siebel CRM IP22.8 using OAuth2” how to configure Siebel to work with the new type of authentication.
In this blog, we will provide detailed procedure how to setup, test and validate that email accounts in Online Exchange are correctly configured and accessible through POP3 OAuth2 Authentication. Microsoft identity platform performs IAM only for registered applications, so firstly your application must be registered with Azure AD,see here. After registration and adding credentials, client secrets, one gets necessary attributes for access.
Following attributes are provided after registration and adding client secrets:
Display name
Application (client) ID
Object ID of Enterprise Application (Service)
Object ID of App Registration
Directory (tenant) ID
Client secret Value
Client secret ID (User client)
These attributes will be used to grant the access.
firstly create principal, where display name attribute, application (client) ID and Object Id of Enterprise Application attributes are used.
Then, give permission to mailbox, use Client secret attribute.
The example of giving access rights to mailboxes can be as follows:
# create service principal
New-ServicePrincipal -displayName exo-pop-siebel-test -AppId 407aXXXX-XXXX-4b4a-8b0b-dc9c6b6XXXXX -ServiceId a5dXXX-XXXf-4ff6-add4-XXXXXXX09faf
# check SP ID
Get-ServicePrincipal | fl
# set access rights
add-mailboxpermission -identity mobi24@mobiliar-test.ch -User a5dXXXXX-15XX-4fXX-add4-b0fee4XXX9XXf -AccessRights FullAccess
After configuration in Azure, we can test and validate the access to mailboxes. For accessing using POP3 and OAuth2 authentication, the first step is to ask for the access token. To get the token, following request can be called:
curl -X POST https://login.microsoftonline.com/directory_tenant_ID/oauth2/v2.0/token -d "client_secret=Client secret Value" -d "client_id=Application (client) ID" -d "scope=https://outlook.office365.com/.default" -d "grant_type=client_credentials"
The successful response looks as follows, token is typically valid for one hour {"token_type":"Bearer","expires_in":3599,"ext_expires_in":3599,"access_token":"access_token …………….."}
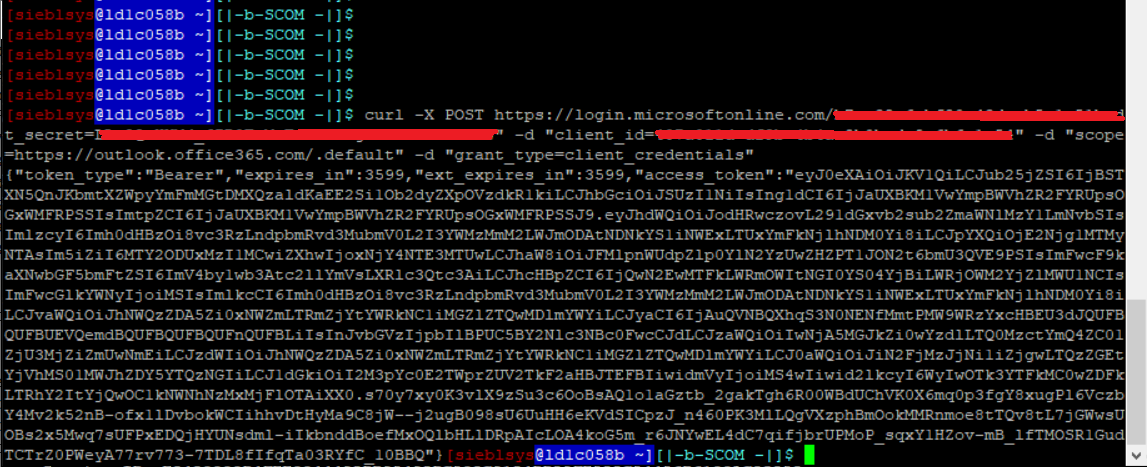
Once we receive access_token, we know that our tenant in Online Exchange is setup correctly and accessible. Using access token, we can try to access to POP3 mailboxes. Using following command we can connect in linux to cloud Exchange server:
openssl s_client -showcerts -connect outlook.office365.com:995 -crlf -ign_eof
For authentication using OAuth2, POP3 command: AUTH XOAUTH2 should be used. OAuth integration requires to use SASL XOAUTH2 format to encode and transmit the access token. SASL XOAUTH2 encodes the username, access token together in the following format:
<base64 string in XOAUTH2 format>
Base64 string is composed as follows:
base64("user=" + userName + "^Aauth=Bearer " + access_token + "^A^A")
where username is mailbox address, e.g. mobi24@mobiliar-test.ch and access_token is one returned in previous step.
^A represents a Control + A (%x01). When you try to compose this string manually, text editor which supports switching into hex codes view and writing of hex codes into the text can be used, e.g. notepad++
Example of base64 encoding :
base64("user= mobi24@mobiliar-test.ch ^Aauth=Bearer eyJ0eXAiOiJKV1QiLCJub25jZSI6IlY2aGVkeEdnSk0ySVpoaEQyLW5uVnJ5WDRzel96OXFmaExPNpYlU….. ILSA2A^A^A")
Encoded base64 SASL string will be now pasted after accepting the command AUTH XOAUTH2. Valid SASL encoded bearer then successfully does the authentication and allows access to mailbox, see following screenshot:
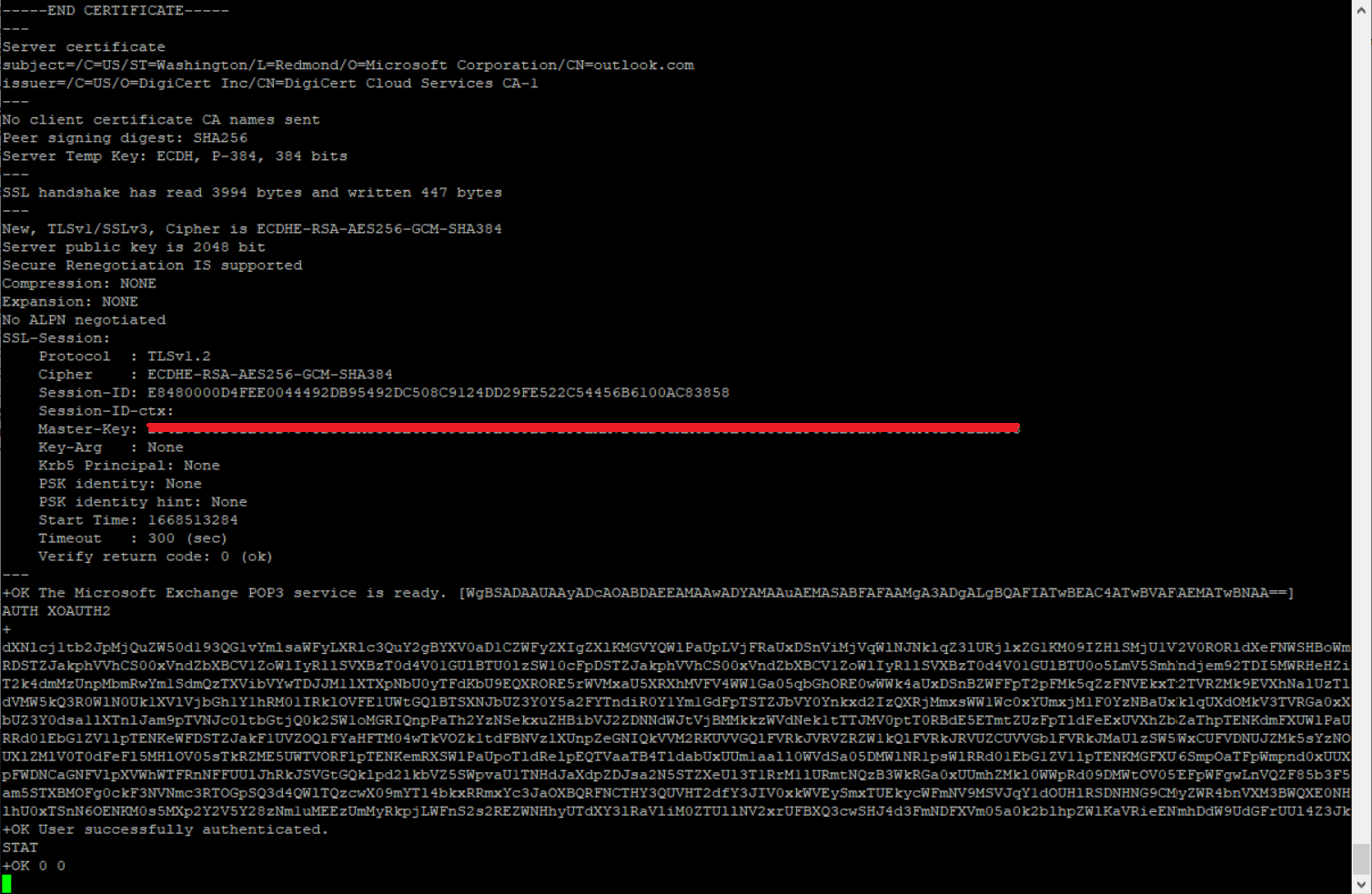
For reference, please see here.
Back to Blog